Organizations face a myriad of data security challenges, such as limited cloud provider controls, misconfigurations, and data sharing concerns. In today’s digital landscape, organizations cannot afford to wait for global rules to crack down on cybercrime. They must proactively address their data security challenges to protect sensitive information, maintain customer trust, and comply with stringent regulatory requirements, all while safeguarding their reputation and competitive advantage.
This blog highlights three clients who successfully addressed these challenges without any disruptions to their business. Read on to discover how Sotero not only enhanced their clients’ data security but also provided additional benefits, including improved access control, compliance, and overall data management.
Client #1: Cloud Data Security
In an era where cloud computing has become increasingly popular, organizations face several data security challenges, especially when cloud providers offer limited security controls.
On top of these limited controls, this client suffered from data misconfiguration that allowed unintended access to unauthorized individuals. They also risked exposing their customers’ sensitive data to breaches and being viewed in plaintext by encryption key holders (such as the cloud provider or database administrator).
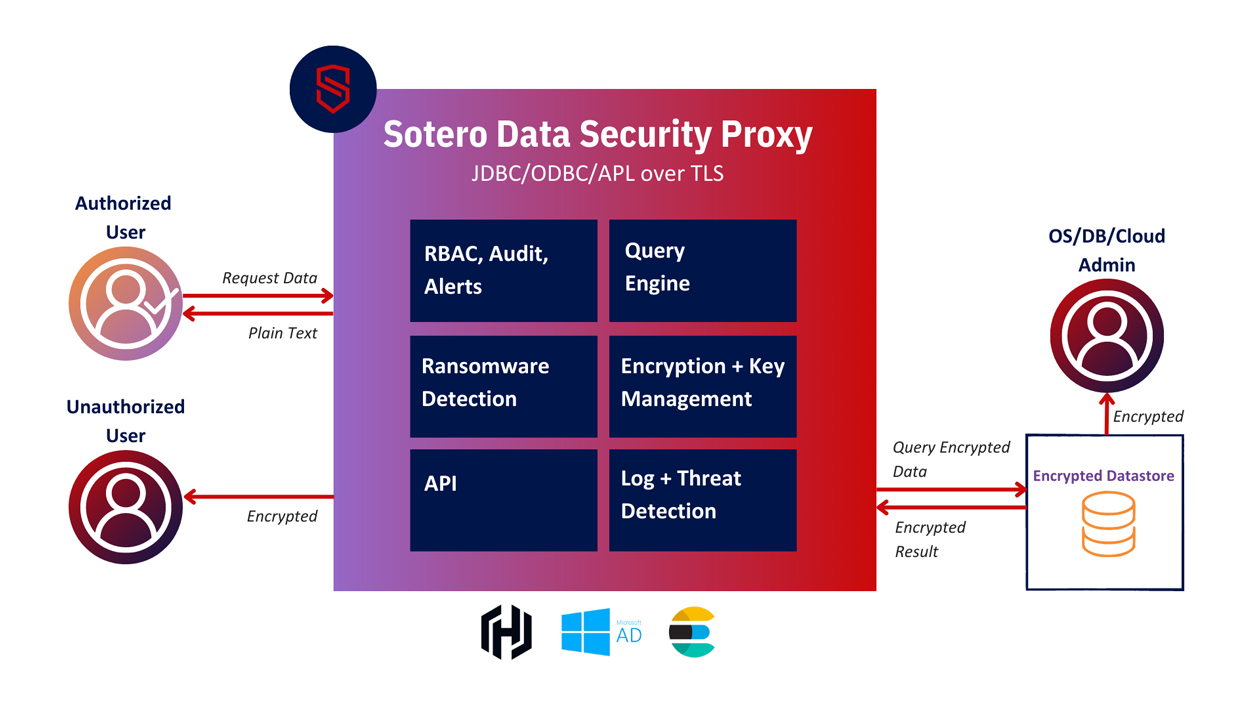
Solution
In order to confidently store and manage its data in the cloud, the client implemented Sotero’s advanced data security platform because:
- Sotero protection goes beyond cloud providers to limit access to files with role-based access controls, preventing unauthorized sharing
- Sotero allows organizations to control their own keys, keeping external parties from access to sensitive data
- Sotero encryption protects data at all stages, including in use, ensuring that even if stolen, the data is not visible for unauthorized users
- Sotero actively tracks all data access requests, creating profiles of data utilization
- Anomaly detection uses machine learning to identify data misuse from insider threats and compromised accounts, blocking access to virtually eliminate data theft
Benefits
Sotero’s all-inclusive data security solution empowered the company to tackle the challenges arising from inadequate security controls offered by cloud providers. By preventing cloud providers and other unauthorized parties from accessing or modifying their data, the company enhanced their data security. Even in the event of a cloud provider breach, the company’s data remained secure due to encryption with organization-controlled keys.
Moreover, Sotero effortlessly integrated with cloud applications and services without requiring any coding. A unified user interface offered insight into cloud data usage and compatibility with industry-standard SIEM tools. Anomaly detection, powered by machine learning, identified and thwarted malicious activities. Concurrently, monitoring all access requests enabled the organization to adhere to regulatory, data governance, and compliance standards. The smooth implementation safeguarded data without affecting user experience, while integrated active ransomware protection guaranteed the security of cloud resources from extortion attempts or potential infections.
Client #2: Data Lake
Data lakes have become essential for storing and managing vast volumes of unstructured data, which often involves access by numerous parties, including applications. However, maintaining governance and ensuring data security within the data lake is difficult, especially if there aren’t any audit trails for modifications to objects.
Solution
To overcome these challenges, Sotero’s data security platform provided the client with robust protection, access control, and compliance:
- Sotero de-identified data in different objects within the lake, protecting customer data and making it available to various users.
- Sotero implemented role-based access controls, allowing for different data control levels on objects to be placed on different user groups. This facilitated multiple groups having access with different visibility levels.
Benefits
Sotero enabled the client to overcome their security and governance challenges, transforming their data lake from a chaotic, free-for-all collection to a controlled repository of unstructured data, streamlining the management process. Simplified management allowed users to access the entire data lake while individual objects were protected with fine-grained access controls using role-based access control (RBAC). Furthermore, in-depth data modification tracking helped maintain compliance with the strictest regulatory standards by ensuring a fully attributable audit trail. Sensitive data remained encrypted throughout its lifecycle, including during transit, storage, and use, providing enhanced security from both external and internal threats.
Client #3: Third-Party Data Sharing
Sharing data is crucial for collaboration and work across organizations, including contractors and vendors. Once data is shared, it leaves organizational control and can be lost or stolen without the original owner being aware or having any control in stopping it.
The client faced the challenge of using existing collaboration solutions that encouraged rapid data sharing without the ability to track or limit what had been shared and with whom. This situation made their data vulnerable to unauthorized access and misuse.
Solution
Sotero’s data security platform addressed these challenges through several key ways:
- Sotero protection limits access to files using RBAC (role-based access controls), preventing accidental sharing with unauthorized individuals.
- Sotero actively tracks all data access requests to create data utilization profiles. Sotero encryption protects data at all stages, ensuring that even if stolen, the data is not visible for unauthorized users.
- Anomaly detection uses ML (machine learning) to identify data misuse from internal threats and compromised accounts, blocking access to virtually eliminate data theft.
- Sotero protection sits between end users and assets, allowing monitoring of cloud data and on-premises infrastructure.
Benefits
Following the implementation of Sotero’s solution, the client experienced a multitude of benefits. They could securely share data with third parties without the risk of unauthorized redistribution. Additionally, unalterable documentation tracked all access requests, providing valuable details on who accessed the data and what actions were taken. This contributed to achieving data compliance and governance requirements through active monitoring, automated alerting, and responses.
Furthermore, the solution offered in-depth visibility that integrated with existing SIEM or IaaS systems, utilizing a single user interface for a comprehensive view of the organization’s information security. The seamless user experience ensured anomaly detection protected data without negatively impacting employees, allowing them to work uninterrupted and unaware of the background tracking and protection.
Sotero’s cloud data deployment facilitated easy adoption, management, and rapid scaling. The solution, which required no server-side software or coding, could be quickly integrated into the client’s infrastructure.
Partner with Sotero
While many security solutions may provide encryption or access control services, Sotero helps you build a cohesive data security approach that goes beyond legacy encryption solutions. Sotero bundles active threat detection with an end-to-end encryption solution. Sotero is the only solution to keep data encrypted throughout its lifecycle, without the need to decrypt data for access or analysis. This technology removes the risk of having to pay ransom for stolen data, instead keeping data protected at all times.
Schedule a demo today to discover how Sotero can help your organization with a defense in depth approach to data protection.
