What is Queryable Encryption?
In an era where data is king, securing it remains paramount. Queryable encryption (also referred to as In-Use Encryption) is a pioneering approach to data security that allows data to stay encrypted even while being accessed or analyzed. Unlike traditional encryption methods, queryable encryption keeps your data shielded not only when it's at rest or in motion, but also during utilization - a pivotal distinction in today's data-driven world.
Why Traditional Encryption is No Longer Sufficient in Today’s Threat Environment
Traditional encryption solutions offer a false sense of security. While they protect your data when it's stored or transported, the moment it's accessed or queried, it becomes decrypted and thus vulnerable. This shortcoming exposes organizations to data breaches, loss of sensitive information, and non-compliance with data privacy regulations.
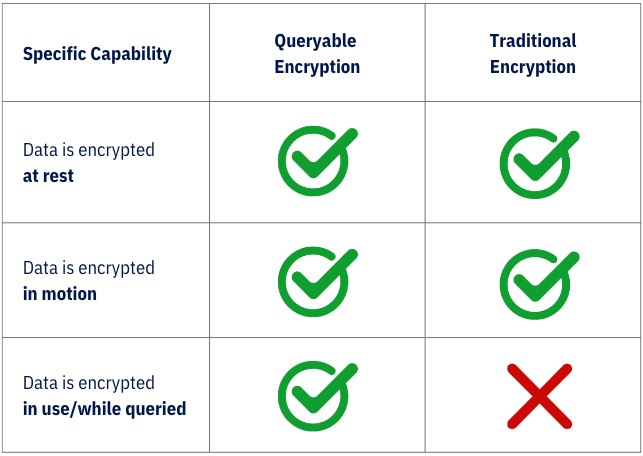
Queryable Encryption Vs. Traditional Encryption
How Queryable Encryption Protects Data 24/7
Sotero is revolutionizing data security with its patented data in use encryption technology. Our unique approach ensures that your sensitive data remains encrypted even while being used or queried. Powered by our proprietary "KeepEncrypt" technology, Sotero renders data useless in the event of a system breach, thus preventing any loss of information.
To learn more about Sotero’s Queryable Encryption, view the datasheet.
Benefits of Sotero's Data in Use Encryption
Sotero's data in use encryption offers several compelling advantages.
1. Your Data is Always Protected
It enables you to keep all your sensitive data encrypted at all times, regardless of whether it is structured data or unstructured data or whether it is on premises or in the cloud.
2. A Single Platform for All Your Data
Our centralized Data Security Platform gives you the control to decide who can access what data and when.
3. Meet Regulations or Stay Compliant
Data privacy regulations that mandate data must be encrypted at all times require that the organization can now prove that data stays encrypted even when it is accessed.
4. Low Performance Tax
Queryable encryption is offered at a granular level, allowing organization to encrypt only their most sensitive data. By not having to encrypt everything, the solution’s low latency is unparalleled, with no impact on user experience.
5. Fewer False Positives
Being able to perform computations on encrypted data directly leads to more accurate results than if you have to decrypt data first, reducing the risk of false positives.
Capabilities of Queryable Encryption over Traditional Encryption
.png?width=2000&height=2000&name=Encryption%20Table%20(1).png)
Encryption Technology
Adhering to the AES-256 standard, all sensitive data is encrypted wherever it resides. This includes all data fields in all applications that adhere to the AES-256 standard as well as heterogenous applications such as ODBC, RDBMS, and JDBC databases, and applications deployed on-premise or in a private cloud, public cloud, or hybrid cloud. Whether you have structured data or unstructured data, it stays encrypted at all times. Download our datasheet to learn more.
Why Organizations Choose Sotero
Organizations worldwide are choosing Sotero for its innovative approach to data security. Our technology allows for secure and rapid data sharing, enables quicker production use cases, and offers unrivaled control over your data. But don't just take our word for it – check out these case studies from our satisfied customers.
Sotero's queryable encryption technology offers an advanced solution for modern data security challenges. Our patented technology and unique approach ensure that your data stays secure at all times – whether it's at rest, in motion, or in use. Download our In-Use Encryption white paper to dive deeper into our technology, or contact us to see how Sotero can help secure your organization's data.
How Sotero Addresses Potential Concerns of In-Use Encryption
Because queryable encryption is a relatively new technology, some information security teams are hesitant to deploy the solution due to concerns around:
- Complexity of key management
- Computationally demanding cryptographic techniques
- Pilot testing
Sotero is a step ahead and has accounted for these potential concerns to help its customers navigate seamlessly through these complexities. Learn more about each of the potential concerns and what Sotero has done to resolve these.
1. Complexity of key management
Sotero offers an automated key management solution that handles the creation, rotation, and deletion of keys automatically and securely. In addition, our technology leverages a centralized key management system that provides you with a consolidated view and control over all encryption keys to reduce your team’s cycles.
2. Computationally demanding cryptographic techniques
Although queryable encryption techniques can be more computationally intensive than traditional encryption methods, Sotero’s patented technology leverages more powerful computing resources and optimizes its code to be highly efficient.
3. Pilot testing
Sotero understands the complexities of an organization’s security stack and architecture and offers a paid pilot for you to test our platform on a smaller scale before scaling with a larger deployment. If you are interested in learning more, please fill out out demo form we will be in touch shortly.


